WSE IT’s Multi-Factor Authentication Overview
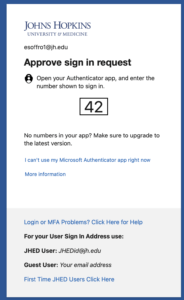
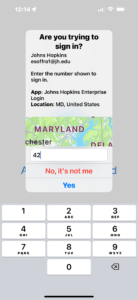
A majority of systems at JHU are now using multi-factor authentication, which is sometimes called MFA, two factor, or step-up authentication. Examples of systems that already use MFA are your online W2 and Employee Self Service (ESS) in myJH, the VPN client, and your webmail, when traveling internationally. Often, it will look like this in your web browser. You will first be prompted to enter your normal JHED and password, but then will be prompted to either provide some additional information or to click a button in an app on your cell phone (or even on your smartwatch!).
For those with smartphones, this push notification to the authenticator app is probably the easiest (and coincidentally, the most secure) method, but there are different types of MFA at Hopkins, including time-based generation of numbers and text message alerts. In all cases, the extra authentication acts as a second password for your account, and because each use of MFA is a unique occurrence it provides a very high level of security because it can’t be reused if it is stolen.
Though the IT@JH documentation does a good job at step-by-step instructions, it can be hard to find and doesn’t provide context-specific for the WSE community. This page tries to tie together the how-to instructions with the bigger picture.
Sections
- I HATE Multi-Factor Authentication
- It Doesn’t Have to Be Painful
- How to get started
- Is convenient also secure?
I HATE Multi-Factor Authentication
We know, but it’s important. Passwords, because they’re easy to guess — or steal — are essentially obsolete for anything that you really care about. You need to care about your JHED account because it has access to sensitive information like your payroll information, financial and student information, your email, and so on.
Adding a single-use second factor adds considerable protection to your account — in addition to a password, which tends to be static and can be compromised in many ways, a secondary factor like the MyIT Login Code becomes useless after a minute. This makes most traditional hacking techniques ineffective against your accounts.
It Doesn’t Have to be Painful
Using the MyIT Login Code doesn’t need to be painful. Historically there has been an emphasis on using SMS messages for these codes, but that’s frustrating. You don’t want to have to type to use the codes, and when traveling it can be expensive or impossible to get an SMS message. The smartphone app just needs a data connection to get the push notice – when traveling, you don’t need to worry about having SMS service. Just hit type in the two-digit confirmation code you see on the webpage and you’re done.
How to get started
This video shows how to get the app configured for your smartphone. You can click here to enroll (this is the link mentioned in the video).
We encourage everyone to add a backup MFA method. This is to ensure minimal disruption to your account access should you decide to change phones, phone numbers, or computers. Without a backup MFA method, you will need to call IT@JH’s help desk to have them sort out your account.
Is convenient also secure?
Convenient is also probably secure, in this case. Certainly more secure than a password alone.
- Without a time-based or device-push passcode, bad actors have it pretty easy to hack your password. They can make a lot of guesses at the password over time using automated tools that are shockingly good at guessing them. Further, if a password you use on more than one site is compromised, the extra passcode would keep them from reusing the stolen password on Hopkins systems — they’ll get past the password but won’t be able to guess the MFA gateway.
- MFA codes expire quickly, so even if your JHED password and MFA were intercepted (by a keylogger program, or through an insecure network) attackers still won’t have long-term access to your data.
- Systems that rely only on SMS have been compromised many times. The bad actor just convinces your carrier to move your cell phone to their device and they’ll start to receive your messages. That transfer doesn’t affect the push messaging for the MFA apps.
- If your phone is lost or stolen, reset your secret key along with your password when you get a device.